This is the most in-depth review of the startup Reflectiz, available anywhere in the web! We review variety of aspects regarding the company, including: the pain, solution, technology, market, team, investors and beyond. We do this while sharing a honest and open interview with the co-founder and CEO of Reflectiz, Idan Cohen.
Let’s Go!
Intro – The Writer’s Experience
It was certainly my pleasure to interview, Idan Cohen, CEO of Reflectiz. After meeting with hundreds to thousands of entrepreneurs, I got used to how knowledgeable and sharp they usually are. In similar also Idan knows his game, but he is also brutally honest. To a degree of fault. 🙂
Reflectiz’s field of operation is quite different from what I’m used to seeing in the cyber security sphere. It stands out, to the right degree, in my humble opinion: It’s innovative but not too innovative. Reflectiz seems ahead of the market, but there is a market: an emerging yet a substantial one. A market which pays top $ for solutions by Reflectiz and their competition. A market which is legitimized by threats which grab top headlines.

The Pain: Web Supply-Chain, Discovery & Monitoring
“As part of a PoC, we conduct an asset discovery for our prospects. Within minutes we receive the report: the enterprise’s website comprises of dozens of 3rd party vendors. Some of which are open-source libraries. Then I ask our prospects: ‘do you trust all those external vendors? do you track how they handle your sensitive information?
Usually the security officers would be puzzled and admit: ‘we were not even aware of those external vendors. We did not know they are in our site!’”, shares Idan Cohen, CEO of Reflectiz.
Those 3rd party vendors are the reason for the successful wide-scale attacks by Magecart, which include: the British Airways breach (aka Magecart card skimming), Newegg attack, Ticketmaster incident, Macy’s hack and Amazon S3 breach . Those, in addition to some 50,000+ additional domain infections as revealed by CPO Magazine“.
Every organization has a secure software development cycle (SDLC), for releasing new applications. Usually the cycle would go from code-review through penetration testing to auditing.

“But the same does not hold true when it comes to websites”, Claims Mr. Cohen”. With today’s tools, it’s extremely difficult to perform discovery -and-monitoring of your website. The presence of 3rd-party vendors is the reason for that. Those have access to your sensitive data such as user passwords, credit card information, medical records, etc.
Consequently, websites today are the weakest link in the organization’s supply-chain. “Organizations today are unable to properly monitor their website’s external code, and discovering their supply chain”.
Simply put: Organizations do not know which vendors access their sensitive information, or where is it sent to.
The Problem Magnitude
“Today every site is 3rd-party based” claims Idan in quite a broad statement”. This trend has been going on for a while now: organizations use a growing number of 3rd-party code, within their applications and sites. More than ever before. And it’s a big problem!” Idan determines decisively. A problem which Reflectiz solves.
Is this really a big problem at all, I wonder? Idan then pulls a number of incidents. Each demonstrates the problem’s magnitude. “Following the wide-scale attack on British Airways, Wired announced the Magecart groups as one of the ‘Most Dangerous People on the Internet’!
“The growing number of successful attacks by the Magecart groups and alike, speaks for itself. Depending on who’s estimation you believe, we are talking about 50,000+ or even 70,000+ domain infections, and counting”, concludes Idan.
Understanding the Magecart Threat
In cyber terms, Magecart is fairly a new attack vector. It was first introduced in 2016, and in only grows since!
What exactly is this attack vector? What’s characterizes all Magecart attacks? What vulnerability is being exploited? and perhaps most importantly, how can organizations better protect against it?

Web Application Security & Reliance on External Code
Reliance on external sources when developing applications, is not really a choice. It’s part of our lives. In today’s reality, organizations must deliver, and fast. Consequently, organizations can no longer develop all code internally. Rather, organizations rely on tens of external code sources, such as 3rd party vendors and open-source.
When it comes to websites or web applications, understanding the implications of such external sources is quite challenging.
According to Idan, “This leads to a state where organizations completely lose control of their code, and they don’t even know it!”. Organization may have well established controls in place, when it comes to their internal development practices. But when it comes to web applications, traditional controls are ineffective. Modern and inovative controls are required.

How Was Magecart Mitigated so Far?
The traditional solutions are penetration-testing, code-review, minimizing the use of 3rd-party code, compliance-based questionnaires and so on. They are manual, and provide limited coverage.
Why Is the Coverage of Traditional Solutions Limited?
“Mainly because those solutions are testing only the site’s current security level. They are not addressing the fact that third-party components change on a constant basis!”, explains Idan.
“Also, the regular security controls such as WAF won’t help in those circumstances”. adds Idan. Why, I asked? “WAF protects communication between the end user and the site itself. Unfortunately, WAF has a major blind-spot: The traffic between the end-user (which surfs the web) and the third-party vendor. That traffic is not monitored by WAFs. Evidently, WAFs did not issue alerts in previous Magecart attacks”, says Mr. Cohen.

Organizations Lost Control of Their External Code
“Based on our experience”, Idan says, “I can testify that organizations do not know how many 3rd party components are involved in their code”. Then he adds: ”Organizations don’t know which components are there, what do they do, how they do it and most importantly: which sensitive information they access, and send to their own servers!”
Sensitive web assets such as employee listings, financial records, medical records, etc, are shared with many others. In many cases, the application’s architecture is not a matter of deliberate intent. Rather rather it is a result of circumstances, misunderstanding or possibly even negligence.
Lastly, Idan adds: “It is very difficult for organizations to track the external sources which are embedded in their code. Over time the problem only grows larger. As developers change, tracking the code history becomes more complex, etc. Such processes naturally lead to risks and vulnerabilities”.

Website Security – Target Market
Most of Reflectiz’s customers are enterprises in the financial and e-commerce segments. In the near future, Reflectiz plans to raise Round-A funding. That round will act as the enabler to selling to market leaders. Some of which are in relationship with Reflectiz, on regular basis.
The Reflectiz Solution
What is Reflectiz? Refletiz is a platform which conducts a full website discovery and mapping of all 3rd party code. Reflectiz provides a full analysis re: what each external vendor does with the site owner’s users, data and traffic. Reflectiz detects vulnerabilities, privacy gaps and security issues. All this in semi real time, in a robust manner and without human intervention.
As vulnerabilities are detected, Reflectiz then issues automated alerts.
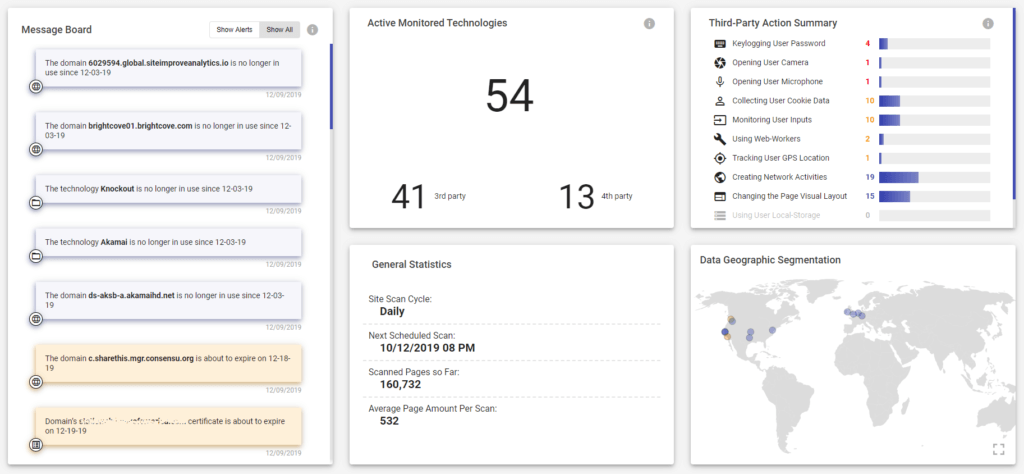
Reflectiz Customers & Target Market
Reflectiz provides value to organizations of all sizes and in all segments. However, we most successfully target enterprises such as: banks, insurance companies, travel, ecommerce, etc. Our ideal prospect manages a websites which contains sensitive information, and plays a valuable role in the company’s business model.
Who in the Organization Benefits from Reflectiz?
The Reflectiz solution is operated by the organization’s security and privacy teams. It delivers value for the Security and Privacy departments, as well as for Digital and IT.
How does Reflectiz Work?
We simulate a user which takes actions in the site. Then we monitor and analyze the website’s traffic. This is done on an ongoing basis. With the information we collect, our algorithm maps the site to detect and alert of vulnerabilities.
We detect anomalies via our behavioral analysis algorithms, which we developed internally, and via dozens of global databases which we utilize.
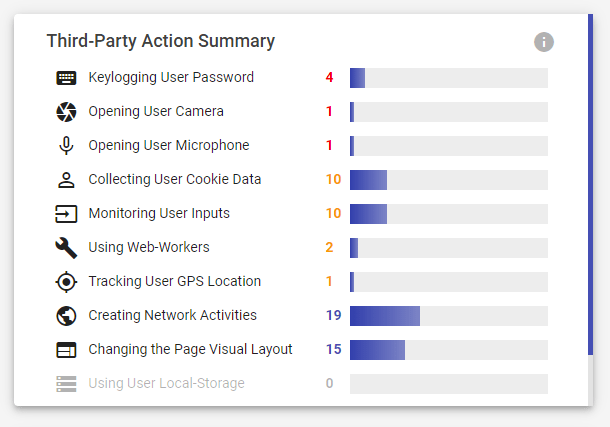
Reflectiz Installation Process
“Setting up an environment is so very easy”, Says Idan. He then continues: “Not only we do live demos at no cost, to prospect’s sites in PoCs, but furthermore: we conduct such live demos on prospects’ s sites, during spontaneous meetings in conferences and expos!”.
Idan takes pride in how easy it is to set up (and sell) Reflectiz to customers: “Our solution does not require installation or long customization of any type, on behalf of the customer. The product is highly automated, agentless, seamless, effortless, everything-less :).
We can scan an entire site from remote, in a robust manner with very limited resources. Most likely, the organization won’t even know we’ve been there!”.
What Does Reflectiz See (the WWW Triangle)?
To what degree Reflectiz is able to analyze a site, I asked. Mr. Cohen answered with confidence: “We see everything. If the site collects information, I know it. I know what information it collects, who collects it, and where it is sent to. We see this as the WWW triangle: Who, What & Where”.

Critical Vulnerability Reflectiz Detected @ Top-5 Largest US Bank
Idan shares of a critical vulnerability which Reflectiz can easily find. Accordingly, they have indeed found it in in numerous sites. Among others, it was found in the website of one of the 5 largest banks in the US!
What is the vulnerability, I asked? “The bank’s website loaded a script from an expired domain!”, Idan shares.
Such a vulnerability allows anyone to easily plant a script in the organization’s site. This is done by purchasing the expired domain, and placing the script in the location it’s called from.
While it sounds quite trivial, this is evidently not so easy to detect. Otherwise, how would we explain that it was found in one of the 5 largest banks in the US (among many other sites)?
In that specific case, Reflectiz immediately notified the bank of the problem. In response, the bank indeed fixed the vulnerability.
Sadly enough, Reflectiz did not get a bounty for sharing this vulnerability. But rather they might have gained something more valuable: the 1st step toward establishing a relationship of trust with that prospects.

To conclude this point, Idan summarizes: “We understand the complexity in protecting applications external code. But so do Magecart, which exploit exactly those vulnerabilities”.
More Real-World Examples
Sample Real-World Vulnerabilities, Detected by Reflectiz
- Let’s take for example Google, which collects credit card information, and then sends it to their servers in Ireland. In addition the accessibility component collects browsers data but only sends it to a location stored internally. If Reflectiz detects any anomaly in this triangle, then an automated alert is issued.
- Here is an issue which we detected among multiple customers of ours. All of which of course fixed it immediately thereafter. By mistake the site’s analytics tool for Russian or Chinese users, was installed on all the site’s user-base. Yes, including American ones. And vice-versa… This little, yet common mistake, results in sending all the US-based user data to China or Russia!
- Beyond just detecting anomalies, there is a strong element of discovery with Reflectiz. For example: It is normally ok for the credit card clearing company to access credit-card information. And yet, the head of security should be made aware of that, right? Otherwise, how could he manage the risks? or put proper procedures in place?
With reference to example number 3, Idan adds: if we look at privacy, I’d probably like my customers to be made aware of such a 3rd party, accessing their credit card information.
“Without knowing who my vendors are, or what data they access or send remotely, how could I manage the risk or pretend to follow best practices? With Reflectiz, organization can have controls in place, thus comply with laws and regulations”, concludes Idan.

Reflectiz – The Team
To my question, Idan honestly opens his heart and shares: “Me and Ysrael always knew we’d establish a startup company together. It wasn’t a question of “if” but rather “when”, says Idan. Previously Mr. Cohen was the CTO of BugSec (an established Israeli cyber firm specializing in Simulations of Cyber Attack and Penetration Testing).
And indeed, in 2016, Idan and his partner Ysrael Gurt have established Reflectiz together. Ysrael Gurt also worked for BugSec at the time, as a web application team leader. “Ysrael is a respected hacker, I think one of the most famous, at-least here in Israel” says mr. Cohen.

To back up such claims, Idan mentions that Mr. Gurt is actually listed in the Google’s Hall of Fame. His resume includes revealing well known attacks, as well as CVE on Facebook, Microsoft and more.
Idan rounds up with optimism “Jokingly, Ysrael always says, that the first funding of Reflectiz did not come from our investors, but rather from those companies, which granted us bug bounties”.

Retrospective – Reflectiz Field of Operation
Let’s map Reflectiz as a company for a moment. I’d say it operates in the field of Third Party Risk Management (TPRM), with strong relevancy to application security. I.e. managing risk re: external risks (code vendors in this case). Such risks are already active in the web application. Lastly, Reflectiz also has a lot to do with supply-chain discovery.
Closing Words
In my humble opinion, as the writer and as a risk-capital person, I believe that Reflectiz are heading towards a great success.
The team which consists of two founders, somewhat scared me at first sight. Both founders are technologists, whereas I was unsure of the CEO’s capabilities as a businessman. But their proven track record (and their market validation included) speaks for itself.
Reflectiz sells in 3 continents, either directly or through VARs. Their solution is ahead of its game. They provide an answer to a real need.
They overtake traditional solution without a blink. But they also have to compete with other startups, such as: Qprivacy, which appears as young and sharp; and source DEFENSE which is the most mature company among the three (backed by JVP, a top Israeli VC).
Initially Reflectiz raised money (aka “grant”) from the chief scientist as well as angel investors. However, shortly thereafter they managed to abandon the innovation authority. This, in my opinion, which was a smart and brave move.
Instead of depending on additional grants from chief scientist, Reflectiz managed to raise money from Marius Necht, a super angel, co-founder of Checkpoint). As Mr. Nech invested in Reflectiz, he naturally joined its board. This investment, by the way, is revealed for the first time herein, at Startups Israel!
Altogether, the Reflectiz team & board are highly capable of growing their company. Obviously, there are significant challenges ahead, and yet, a great opportunity lead by a capable team!
Good Luck Reflectiz!


1 Comment
Sophia Fayans · February 13, 2020 at 12:52 am
Interesting reading.
Beside detailed review of the company, this article actually summarize the real problems in today’s supply chain lifecycle in relation to software development.
Thank you for detailed review and good luck to the team!